The Device Chronicle interviewed cybersecurity expert Daniel dos Santos, Research Manager, Forescout Technologies to learn about the security vulnerabilities in IoT devices security. They have been detected in stacks affecting millions of IoT connected devices.
Security vulnerabilities research
However, IoT strategists can use research such as that on Amnesia:33 as a rallying cry. They can bring their security professionals together with their DevSecOps teams to address IoT device security. In this way, security can be embedded into the development workflows and robust software updates delivered to IoT devices in the field.
Cybersecurity guidelines
In this paragraph, we show how enterprises are getting support in the battle for IoT device security from government. Guidelines are coming from government to help focus enterprises on IoT device security. For example, the US IoT Cybersecurity Act has just passed and ENISA in Europe has published its own guidelines. In effect, the whole supply chain in IOT is under coming under closer scrutiny and this will evolve into clearer responsibilities for the different stakeholders across the ecosystem.
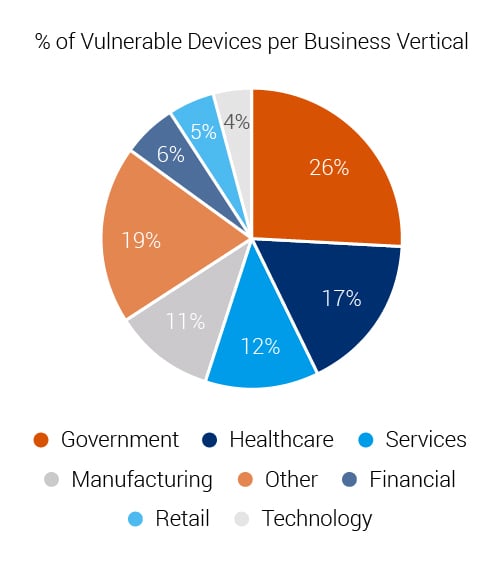
Industrial threats
In this paragraph, we introduce research findings from Daniel Dos Santos, Research Manager, at Forescout Technologies. Dos Santos conducted research into 33 security vulnerabilities in TCP/IP stacks collectively known as AMNESIA:33. Dos Santos points out that these vulnerabilities can affect millions of IoT devices of many descriptions. Critically, the embedded hardware that is used in industrial applications and mission critical systems can be impacted too. In summary, Dos Santos comments “The majority of the vulnerable devices are categorised as enterprise IoT. Several are industrial control and building automation systems which would be classified as critical IoT technologies.”

By way of background, Dos Santos and the Forescout Technologies team were researching embedded devices and TCP/IP stacks. Then they found that these stacks were often included in the software development kits (SDKs) released by embedded hardware component vendors. Furthermore, they found that large IoT hardware vendors were releasing SDKs with vulnerabilities within the stack. It was also common to find these vulnerable stacks in embedded components including connectivity modules and EV boards sold as development kits with example applications. According to Dos Santos, the stacks with vulnerabilities are so widespread that it is difficult for a vendor or enterprise to get a comprehensive account of the risk.
Critical security vulnerabilities
Furthermore, the research found that four vulnerabilities are very critical. They allow for remote code execution. Furthermore, Forescout has developed a proof of concept to demonstrate how these vulnerabilities can be exploited. A malicious actor could take over an IoT device and use it as an entry point or final point of attack.
Serious flaws
In this paragraph, three of the most serious flaws are described. Two affect DNS clients and one affects an ICM PV 6 component of the stack. Moreover, Dos Santos makes the important observation that Denial of Service attacks can often be disregarded as not that critical in the IT world. He quips “PCs and server can be simply rebooted and things return to normal.” However, it is an altogether different story in the operational world. Here, a simple DOS attack can render IoT devices and embedded systems out of operation. In conclusion, many of these devices can be parts of mission critical infrastructure and alarmingly many vendors and enterprises may not even be aware they are using these vulnerable stacks.
Open source and security vulnerabilities
The majority of the stacks with vulnerabilities are open source projects. Moreover, this is where maintenance of software can be challenging. This is because “there are many forks and branches of development from the original source code. It is difficult to get the original developers to create and issue the patches. Furthermore, Device managers find it difficult to receive the required security patches for these vulnerabilities from the relevant 3rd parties. To be clear, closed projects also suffer from similar code fragmentation issues. “Code fragmentation is a big challenge in the embedded world but there are positive initiatives in OA where Github with its security advisories are tackling code fragmentation by issuing upstream issues advice (and warnings) to downstream users.”
Keep a watchful eye
In this paragraph, Dos Santos advises Heads of IOT to keep their ears and eyes open. More vulnerabilities are coming out all the time. Furthermore, Dos Santos advises Heads of IOT to get a disaster recovery plan in place. Moreover, Heads of IOT need to be aware of the prevalence of IoT devices and their bill of materials. For instance, what components are in a device and how might they be affected by the vulnerabilities? Also, what is the security posture of these vendors? When a vulnerability comes out, is the vendor vocal and investigating them, or sweeping it under the carpet?
CERT on the case
Importantly, government and international regulators are on the case. For instance, the four international CERT agencies are in the process of contacting the hardware vendors. However, many vendors are staying tight lipped and not revealing whether or not they have had confirmed issues with these vulnerabilities.
Remedies
In this paragraph, Dos Santos advises on some remedies to the problem. He says patching is the best approach to get full immunity from these vulnerabilities. However, due to the code fragmentation or gaps in knowledge on the extent of the exposure to the threats, this is not always easy for enterprises. Ultimately for Dos Santos, it’s about working towards having more secure platforms in the future for both hardware and software. Furthermore, development practice must improve to look for empty patterns where bad development and code practices arise, identify them and correct them.
Combatting security vulnerabilities
Finally, Dos Santos and Forescout are continuing the good work through Project Memoria . Dos Santos describes how several TCP/IP stacks have been analysed at the same time and compared to previous results. This work has produced a set of recommendations against vulnerabilities. Project Memoria continues to identify vulnerable devices. It also provides an open source script that can be run on a network to detect if devices are running these vulnerabilities. In conclusion, IoT leaders should take note and also look into the Triangle of Trust .

